TryHackMe Security Footage
TryHackMe Security Footage
Analyzing file
First, download provided .pcap file
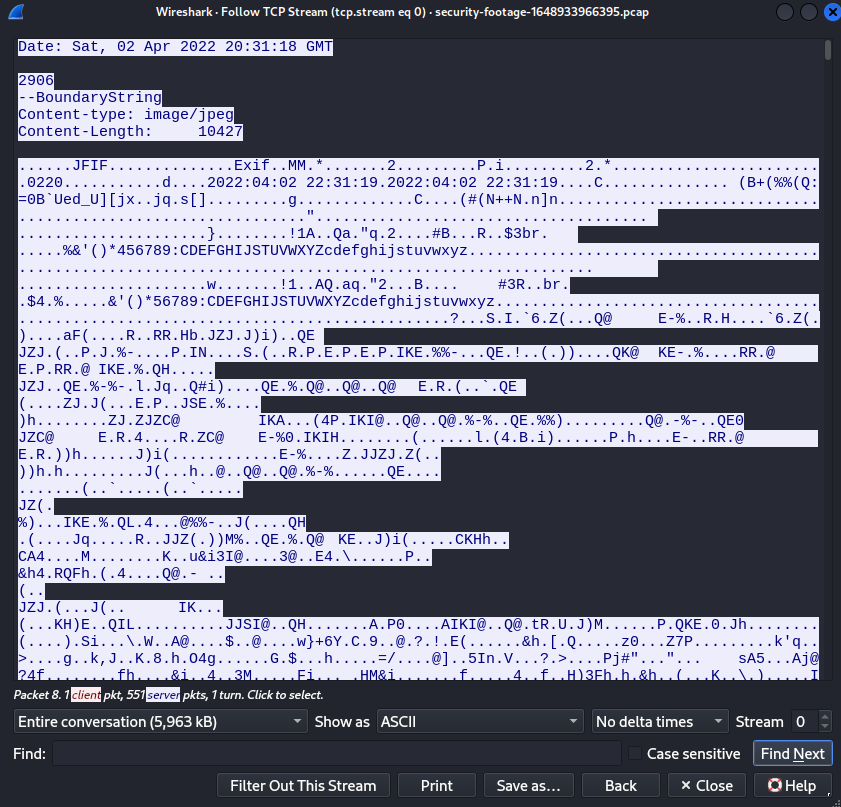
After downloading pcap file and opening it with wireshark follow tcp stream that contains encrypted traffic. Notice that stream starts with JFIF header - meaning that a JPEG file within that stream.
Files recovery
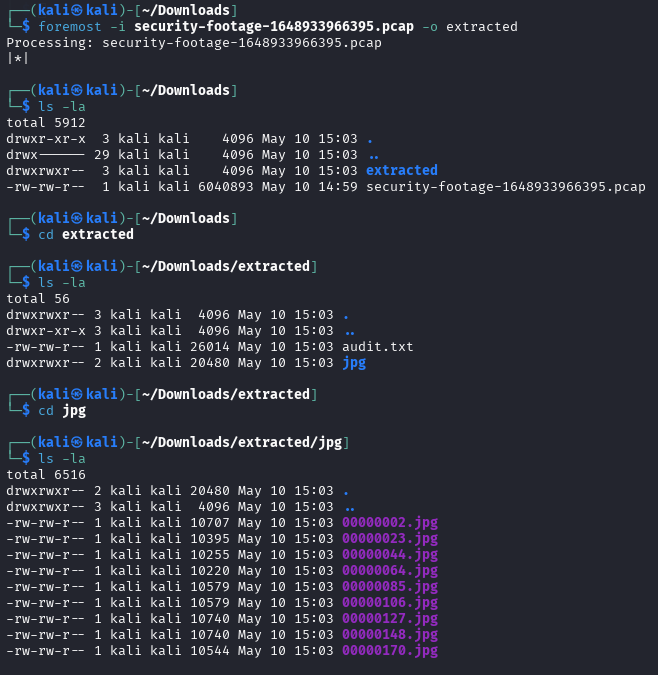
To recover files use foremost with this command
1
foremost -i security-footage-1648933966395.pcap -o extracted
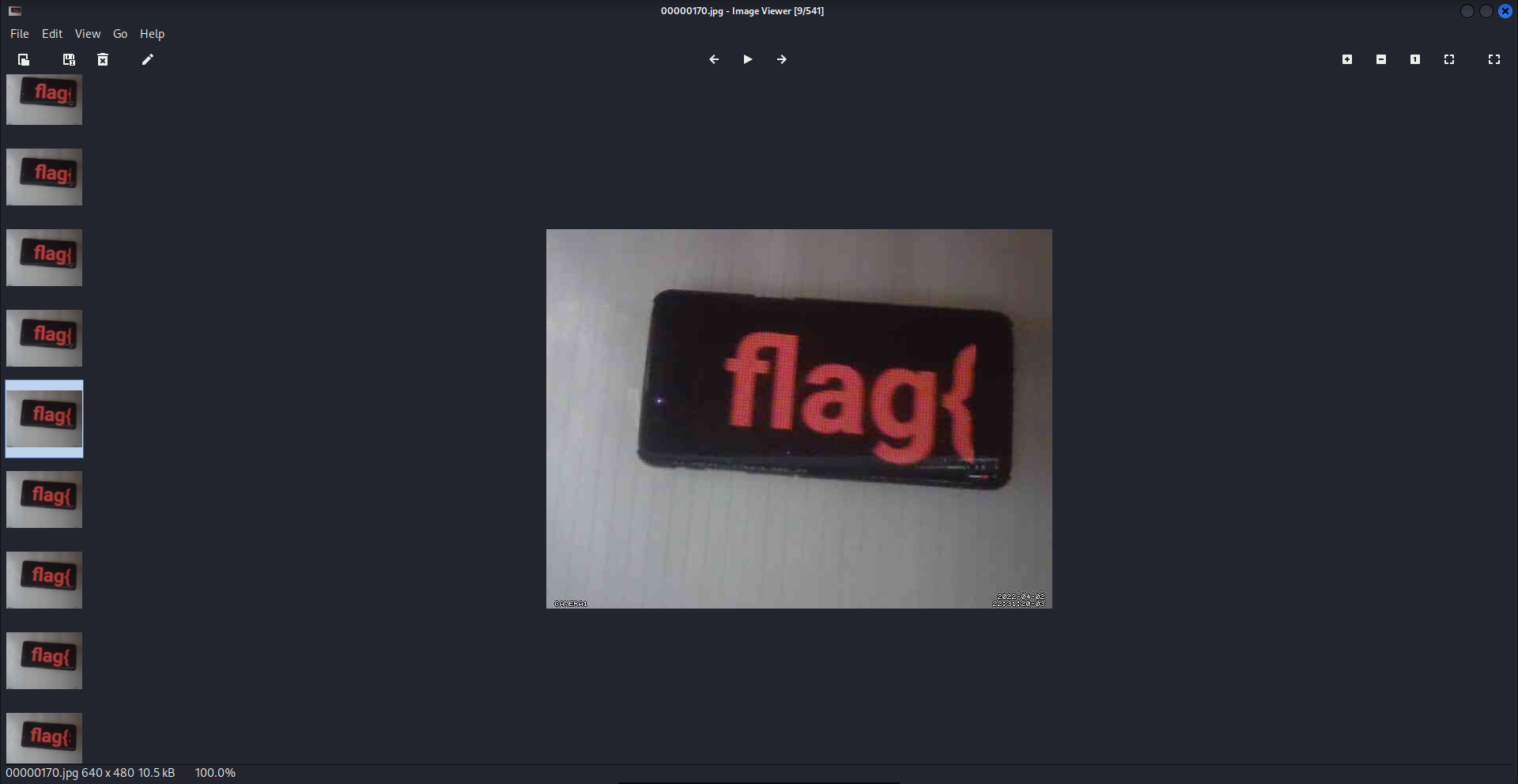
Once images were extracted, open them to reveal the flag
This post is licensed under CC BY 4.0 by the author.